Protect Your Images with Strong Hardware Encryption
Review by Erik Vlietinck
The ToughTech Secure m3 is an external 2.5″ drive enclosure for encrypted file storage. It comes with three hardware encryption keys. The company also offers an encryption key creator tool for when you need to generate your own keys.
The ToughTech Secure m3 is a dark-gray aluminum enclosure with red ABS front and back bezels. The unit is Kensington-lock ready, it’s handheld (not much bigger than the 2.5″ drive it’s designed to contain), and is powered via its USB 3 port. It comes with three small mini-USB plugs that are actually your encryption keys (they’re identical, so three people can decrypt the drive). In the box you’ll also find three lanyards and some other things with which to label the drive and keys.
The unit’s security comes from hardware-based 256-bit AES encryption that protects data well. A 256-bit private key will have a number of possible combinations that’s 78 digits long. To keep your images and video secure, I’d say it’s safe enough.
To start up the ToughTech Secure m3, just plug it into your computer’s USB port with the encryption key removed. In this case, the drive won’t mount. Plug in the key, and it will mount in Write-Protect read-only mode. Once you’ve plugged in the key after plugging in the USB interface, the unit will only switch to write mode when you unplug it again and press-and-hold the front button with the encryption key inserted.
The ToughTech Secure m3 encrypts the entire drive, including boot sector, file allocation table, OS, and temporary and swap files, and it encrypts/decrypts at full disk bandwidth operation. Contrary to what it says on the web page, though, this does come at a small performance cost. My SSD was about a third slower compared to connecting it bare. ■






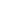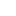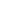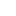
You say it performs better bare. Can you remove the drive from the enclosure and access data fully un-encrypted? That was a huge problem with many early hardware encrypted drives. Only the controller board required a pin for drive access control. The data on the drive was left open to being used by another controller.